Posted by: TAZ Networks on October 19, 2015 at 9:19 pm

A strong antivirus, a solid backup program, and a little education are your best defense when CryptoLocker and other ransomware comes to call.
Almost two years ago, we ran an article about ransomware, a horrific scam that locks up your data and demands payment to get it back. If you don’t pay, the threat goes, they delete all your data and throw away the recovery key.
In just the past few months, we have seen numerous ransomware attacks, mostly from CryptoLocker, the virus named in our initial article. Because of this, we have stepped up our security game, installing an additional, more powerful antivirus for many of our clients — at our own expense.
Why? One, because we care about your company and your data. Two, because fixing these ransomware attacks eats up a ton of our techs’ time, which would be better spent helping you make your technology work better.
However, no antivirus is 100% effective, and, sadly, many of these virus attacks are self-inflicted by users who are duped into clicking on malicious email links and attachments. So, what are some best practices for defeating ransomware and other cyberattacks?
Back It Up, Back It ALL Up
Backups, backups, backups — there’s a reason we go on and on about them. Besides just being a good idea for that occasional “oops” deleted file, a solid backup program is the only known way to recover your data after a ransomware attack. A good backup will save you from having to pay to recover your data from ransomware.
Backup solutions range from a simple offsite data transfer to a full-bodied server replication program like our Standby Server. While swapping out hard drives at your local office is better than nothing, we are now recommending offsite backup to our clients as a more secure solution.
Don’t Be a Phish.
Phishing (email fraud) continues to be a problem because phishing WORKS. Scammers are getting more and more clever, using subject lines like “Resume” or “Invoice” to get you to open their email and download the attachment — which then attacks your network.
We can’t be more clear about this: Do not open attachments from strangers. Got a slightly-odd, unexpected email from someone you know? Give them a phone call to verify it before opening. Unsolicited resume when you’re not hiring? Risk missing out on that perfect employee and just delete it. If it feels “Phishy”, it is.
One extra layer of protection from phishing scams is a quarantine product, such as the built-in spam protection from Microsoft 365. Take a look at the screenshot of Heather’s quarantine notification below.* Depending on your customized settings, the quarantine will capture newsletters you don’t read anymore, sales pitches from companies you don’t want to do business with, and the slightly-creepy, vague subject line. You can then block individual senders, entire domains, or just delete the notification and be done with it.
We’re always happy to sit down and review your network security. Give us a call if you want us to take a closer look for you.
*The product in the screenshot has been discontinued. We currently recommend Microsoft Defender for Office 365 for next-level email protection beyond Microsoft 365.
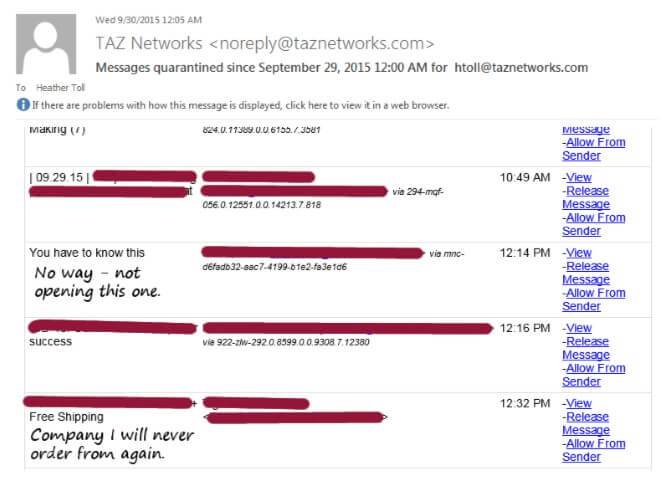
Quarantine questionable – and just plain annoying – emails so you can review them safely before opening.