Posted by: TAZ Networks on March 24, 2017 at 2:30 am
“Yahoo? Isn’t that just personal email? And who even uses Yahoo for email anymore?”
If you asked these questions after hearing about the Yahoo email breach, you’re not alone. The thing is, it doesn’t matter that it was specifically Yahoo that was hacked. But the method the hackers used, and how they used the information they gained are very relevant for even small companies. The results of a targeted attack like this can have serious consequences for your business.
According to an article at CSOonline.com, an email claiming to be from a trusted contact was sent to one or more Yahoo employees. (This is known as spear-phishing.) At least one person was fooled and sent secure information, giving the hackers the access they needed. As the article points out, when it comes to a spear-phishing attack, “it only takes one person to click on a link.”
The details of what the hackers did next is pretty interesting, from a cybersecurity perspective. If you’re interested in that sort of thing, check out the article if you have a few minutes.
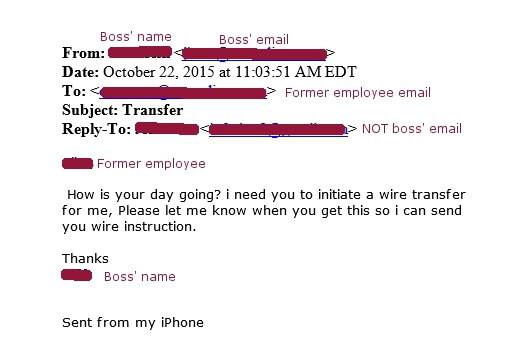
Spear-phishing attempt using a spoofed email. Fortunately, our client knew something was wrong, and contacted us to verify and take care of the problem.
Why should you care?
If you’re not interested in the details and want your cybersecurity efforts to “just work,” why should you care about this Yahoo breach?
The fact is that any business, even a small business, can be targeted. Faked emails look convincingly like the real thing. They often slip through spam filters. And they can wreak havoc on your business. The National Cyber Security Alliance reports that one in five small businesses have been victims of cybercrime in the last year.
Sometimes hackers are after straight-up cash, as in the wire transfer scam. Other times they want financial information, like the W-2 scam. Or maybe they are trying to hack specific people. While targeting hacking was the initial goal of the Yahoo breach, 500 million Yahoo accounts are now compromised, with account names, passwords, and more for sale on the dark web.
So how do you protect your business?
How to “spearphish”-proof your business
- Identify information that should never be requested or sent via email or text. This might include: credit card information, employee W-2s, passwords, patient or client identifiable data, etc.
- Set policy for handling these items.
- Educate staff on the dangers of spear-phishing and the new policies you have set.
As an IT company supporting small businesses, we work day and night to protect our clients from these attacks – and unfortunately we see, on a regular basis, hardworking entrepreneurs being financially devastated by these lawless scumbags. We are determined to warn as many businesses as possible of the very real threats facing their organization so they have a chance to protect themselves and everything they’ve worked so hard to achieve.